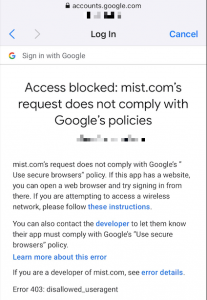
Schools that use Google for Education can have hundreds of accounts that can be leveraged in many ways. One of those ways is to give access to a particular SSID on the school’s WLAN. This allows easy administration and accounting of who is using the WLAN. However, Google decided to block embedded webviews on September …
Aug 25 2023
Find a Loop in Your Juniper / Mist Network
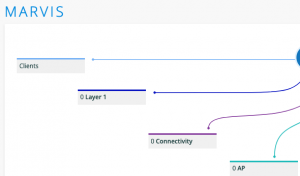
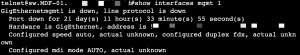
Recently, I customer was saying they were having issues on their new Mist WLAN. Marvis is a great tool but it failed me on this one occasion. I looked at the Service Levels for the network and then notice in Insights / Events all sorts of Events for AP Reflection. I asked several Juniper folks …
May 15 2023
Enable Wi-Fi 6E in Ubiquiti
So you got a new UniFi U6-Enterprise AP? You plug it in. Get a new 6 GHz SSID configured. Push the updated configuration. Then you wait. And wait. Nothing. It seems that Ubiquiti enables outdoor mode on the indoor APs by default. Enabling the outdoor mode on Ubiquiti devices allows the device to operate at …
Feb 20 2023
Ruckus Social Media Login Using Google
Available as of version 6.1.0 Step-by-step guide Begin with Ruckus Steps Step 01In the vSZ GUI, navigate to ‘Network > Wireless LANs. Then navigate to the Zone you wish to add the Social Login SSID. and select ‘Create.’ Step 02Name the WLAN and SSID. Then use Standard or Guest as the Authentication. Then choose Method “Open.“ Step 03Encryption Options use WPA2 for Standard SSID or None for Guest. Step 04Scroll down to Guest Access …
May 16 2022
Useful Ruckus CLI Commands 08.0.95
Switches Configurations Change password on switchenableconf tusername super password BR549JrSmplesexitwrite memory Connecting to the vSZ Speed up the process of the switch connecting to the vSZenablemanager disconnectconf tno manager active-list x.x.x.1 x.x.x.2manager active-list x.x.x.1exitmanager connectshow manager statuswrite memory APs Access AP from Switchssh 10.99.0.73 Have AP phone homeset scg ip x.x.x.x Factory Reset APset factoryreboot
Jan 11 2022
Useful Aerohive CLI Commands
page updated 11 JAN 2022 HiveManager Classic VHM: Working with MAC / PPSK Bindings The easiest way to access the PPSK Server AP is to access it via the SSH Client Helpful commands are: show userThis will show all users the AP has knowledge of. This comes from the Authentication column of “2 – Configure …